AnarchyGrabber3
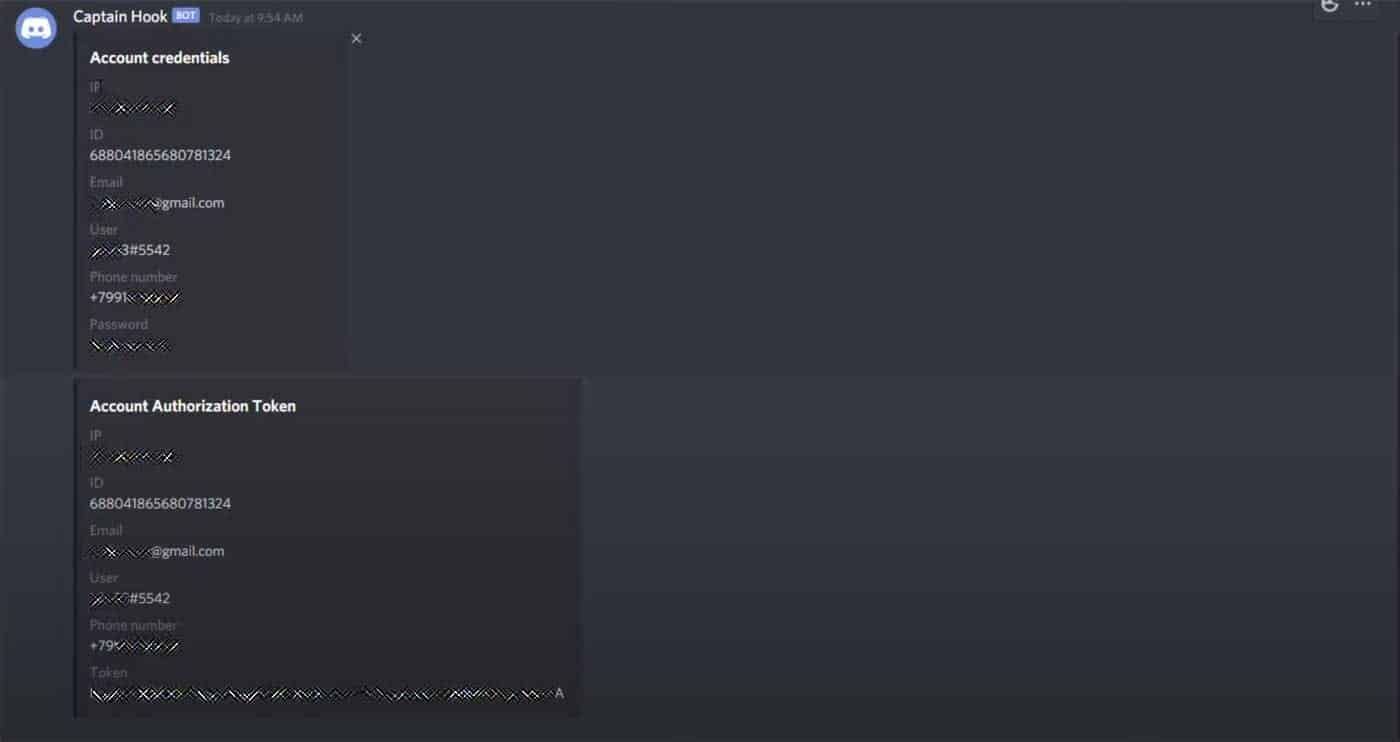
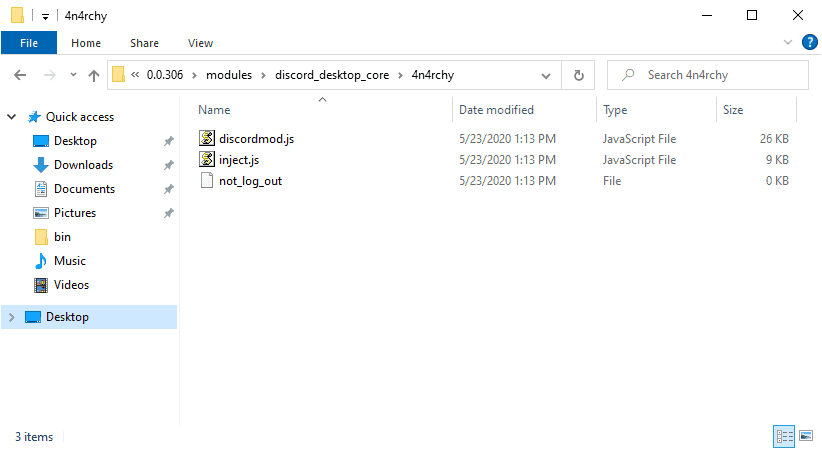
Reported by MalwareHunterTeam, the AnarchyGrabber3 uses pretty much the same methodology of its previous version. The last version, AnarchyGrabber2 was updated in April for debunking antivirus softwares and stealing the credentials safely. And now, this new iteration would comprise all of that and also, disable 2FA and spreadable to others via simple social engineering techniques. AnarchyGrabber is a persistent Discord attacker, as it’s continuing to develop with new features and spread for free on YouTube platforms or other groups. It starts with faking as a game cheat, copyrighted software of hacking tool, but instead modifies the JavaScript files if Discord client. More specifically, it Discord’s index.jx files, and dump malicious files like discordmod.js and inject.js from 4n4rchy folder. Upon successfully being implanted, it will then logout the user from Discord and asks him to log in again. Now, it will log the login credentials while re-logging via Webhook and sends them to the hacker. In this process, it will also disable the two-factor authentication to pass through freely. Things that are stolen here are the user’s email address, IP address, plaintext password, user token, and login name.
How to Check?
Further, it’s also capable of operating according to hacker’s commands remotely. Thus, it can be used for impersonating the victim and spreading the malware to the victim’s friends also. Well, experts have also suggested a way to check whether you’re compromised or not. Navigate to Discord’s index.js file in %AppData%\Discord[version]\modules\discord_desktop_core with Notepad and look for the code looking like this: “module.exports = require(‘./core.asar’)”. If your app has no other code, then it’s safe then. Via: BleepingComputer